
Simplify role management and discovery with Oracle Identity Role Intelligence
↕0♥0S

Simplify Migration and Upgrade using the Oracle Access Management Snapshot Tool
↕0♥0S

Simplify Graph Analytics with Autonomous Database
↕0♥0S
Signing up for an Oracle Cloud Free Promotion
↕0♥0S

Signing Documents Electronically in Oracle Content and Experience Cloud
↕0♥0S

Sign Into Oracle Cloud Console and Create an Additional OCI IAM identity Domain
↕0♥0S

Sign Case Report Forms and Case Report Books
↕0♥0S

Sign Case Report Forms and Case Report Books
↕0♥0S

Show your Wordle skills with Python and Autonomous JSON Database
↕0♥0S

Sharing Files and Folders with Oracle Content and Experience
↕0♥0S

Sharing Files and Folders in Oracle Content Management
↕0♥0S

Sharding Middleware to Achieve Elasticity and High Availability in the Cloud
↕0♥0S

Setup your Oracle Database Migration to OCI in the blink of an eye
↕0♥0S

Setup and Use Oracle Ksplice - Rebootless Updates
↕0♥0S

Setup Cockpit Web Console to manage KVM on Oracle Linux
↕0♥0S

Setting the Oracle Enterprise Manager Software Library User Password
↕0♥0S

Setting the Maximum Upload File Size for Self Service Users
↕0♥0S

Setting the Cloud Administrator Password
↕0♥0S

Setting Up Your Service
↕0♥0S

Setting Up Visual Builder Studio for Oracle Cloud Application Extensions
↕0♥0S

Setting Up Visual Builder Studio for Oracle Cloud Application Extensions
↕0♥0S

Setting Up Secure FTP & SFTP on Oracle ZFS Storage Appliance
↕0♥0S

Setting Up SSH Public Keys for Password less Access on Oracle ZFS Storage Appliance
↕0♥0S

Setting Up Application Server Connections in JDeveloper
↕0♥0S

Setting Self Service User Portal Preferences with Oracle Enterprise Manager Cloud Control
↕0♥0S

Setting Properties for a Column Using Oracle BI EE
↕0♥0S

Setting Preferences for Oracle BI EE
↕0♥0S

Setting Permissions in Oracle Linux Automation Manager
↕0♥0S

Setting Incidents and Email Alerts in Oracle GoldenGate Enterprise Manager Plug-in
↕0♥0S

Setting Credentials in the GoldenGate Enterprise Manager Plug-in
↕0♥0S
Set up an alert rule
↕0♥0S

Set up TMS Coding in a Study
↕0♥0S
Set up Identity Orchestration between Oracle Access Governance and a Flat File Connector
↕0♥0S

Set up DMW for Coding in TMS
↕0♥0S

Set Up the MFT Embedded sFTP Server - Managed File Transfer
↕0♥0S
Set Up the Desktop and Mobile Apps for Oracle Content Management
↕0♥0S

Set Up and Log In to Your First Oracle Container Cloud Service Instance
↕0♥0S

Sesame Software opens up your data lakes on OCI
↕0♥0S

ServiceNow's Single Pane of Glass Manageability of OCI Resources
↕0♥0S

Service Requests and SLAs - Level 100
↕0♥0S

Service Level Management for OBIEE using EM 12c: Part 3
↕0♥0S

Service Level Management for OBIEE using EM 12c: Part 2
↕0♥0S

Service Level Management for OBIEE using EM 12c: Part 1
↕0♥0S

Service Communication Proxy Overview
↕0♥0S

Serverless control of your cloud instances with Micronaut and functions
↕0♥0S

Serverless Functions the easy way
↕0♥0S

ServerPools
↕0♥0S

Server Life Cycle Management with Oracle Enterprise Manager
↕0♥0S

Selective access to the public internet using OCI Network Firewall
↕0♥0S

Selective access to SaaS services using OCI Network Firewall
↕0♥0S

Selecting Software Sources for Oracle OS Management Hub
↕0♥0S
See OCI Search with OpenSearch in action
↕0♥0S

Security for Mobile, Cloud and Social platforms (Recorded Webcast Event)
↕0♥0S

Security Rules and Monitoring/Events
↕0♥0S

Security Overview - Level 100 - Part 9 - Secure Hybrid Cloud
↕0♥0S

Security Overview - Level 100 - Part 8- Secure Hybrid Cloud
↕0♥0S

Security Overview - Level 100 - Part 7 - Visibility
↕0♥0S

Security Overview - Level 100 - Part 6 - Security Control (Resource Access)
↕0♥0S

Security Overview - Level 100 - Part 5 - Security Control (Authorization)
↕0♥0S

Security Overview - Level 100 - Part 4 - Security Control (Authentication)
↕0♥0S

Security Overview - Level 100 - Part 3 - Data Encryption
↕0♥0S

Security Overview - Level 100 - Part 2 - Customer Isolation
↕0♥0S

Security Overview - Level 100 - Part 10 - Verifiably secure infrastructure
↕0♥0S

Security Overview - Level 100 - Part 1 - Shared Security Responsibility Model
↕0♥0S

Securing applications and data with advanced user authentication
↕0♥0S

Securing a Schema from DBA Access on Oracle Database 12c
↕0♥0S

Secure, observe, and connect microservices with OCI Service Mesh
↕0♥0S

Secure your Oracle Database Configuration using Industry Standard CIS Benchmarks
↕0♥0S

Secure your Database using Data Safe
↕0♥0S
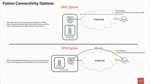
Secure On-Premise printing from Oracle Fusion Applications using OCI
↕0♥0S

Secure Coding Guidelines for the Java Programming Language
↕0♥0S

Searching the Catalog Using Oracle BI EE
↕0♥0S

Searching for Log Entries Using Oracle Log Analytics Cloud Service
↕0♥0S

Search for Packages in Oracle OS Management Hub
↕0♥0S

Search Container Registries with Podman on Oracle Linux
↕0♥0S











































































